Information Security
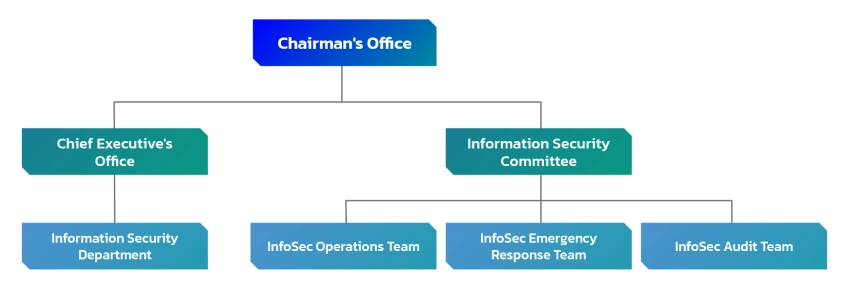
I. Organization
To strengthen information security management and ensure the security of data, systems, and networks, we have established an Information Security Department. This department serves as the dedicated unit for information security, responsible for planning and executing information and communication security affairs. Additionally, an Information Security Management Committee has been formed to oversee the operation of the information security management system. The committee identifies internal and external issues related to information security and assesses the requirements and expectations of stakeholders on information security within the group.
II. Information Security Policy
Our company has established a cybersecurity policy in compliance with applicable laws and regulations. This policy clearly declares support for cybersecurity objectives, providing guidelines for all employees to follow. The goal is to minimize the impact of any cybersecurity incidents, continually operate and enhance the cybersecurity management system, and safeguard the interests of our company and consumers.
Scope of application
All employees of the Group (including full-time employees, temporary employees, contract employees, temporary employees, etc.), manufacturers and their personnel who have business dealings with the Group, and visitors of the Group shall comply with the Compliance.
Information Security Objectives
- To ensure the confidentiality of the Group's information assets, implement data access control, and only authorized personnel can access information.
- To ensure the integrity of the Group's information operation management and avoid unauthorized modification.
- To ensure the continuous operation of the Group's information operations.
- To ensure that the Group's information operations comply with the requirements of relevant laws and regulations.
Information Security Controls
- Establishing an Information Security Management Committee to oversee the operation of the information security management system. This committee identifies internal and external issues related to the information security management system and assesses the requirements and expectations of stakeholders on information security within the group.
- The Information Security Management Committee is committed to maintaining information security, continuously improving the quality of information security, and reducing the occurrence of information security incidents to safeguard the rights of customers.
- The information security management system documents should be updated in a timely manner, and there should be a clear management mechanism for the protection of records.
- Regularly conduct information asset classification and risk assessment.
- All personnel within the group have a responsibility and obligation to protect the information assets they own, keep, or use."
- Job assignments should consider functional divisions, and the scope of job responsibilities should be clearly defined to avoid unauthorized modifications or misuse of information or services.
- For personnel, on-site and dispatched personnel, and visitors from business-related vendors who require access to the information assets of the group, necessary audits should be conducted. These individuals also bear the responsibility of protecting the information assets of the group that they hold, keep, or use.
- Developing a continuity operation plan for information operations based on business requirements and conducting regular testing and drills.
- Regularly monitoring information security indicators to maintain the effectiveness of the information security management system and control procedures.
- Ensuring the safety of work areas and locations to prevent theft or damage to information assets.
- Implementing communication security management.
- The development, modification, and implementation of information operations or procedures must comply with and adhere to the stipulated information security objectives.
- All applicable parties should remain vigilant for any occurrence of information security incidents, security vulnerabilities, or potential violations of security policies and regulations. They should promptly report such incidents in accordance with the established procedures.
- Complying with relevant internal and external legal regulations, establishing necessary control procedures, and regularly conducting information security audit operations.
- Implementing mobile device security measures to manage the risks associated with the use of mobile devices.
- Information security-related issues should be incorporated into information operation project management.
III. Information Security Management Measures
| Manage projects | Management Measures |
| Personnel safety |
|
| Information Asset Security |
|
| Access Control Security |
|
| Key Management Security |
|
| Physical Environment Security |
|
| System and Network Security |
|
| Operational Continuity Security |
|
IV. Resource Allocation for Information Security
- Establish an information security department as a dedicated unit for information security, including a security head and two security personnel.
- The information security department and other units hold a monthly meeting to confirm the implementation policy of information security controls and track known improvement items.
- The Information Security Officer convenes an information security management review meeting at least once a year, reporting significant internal and external issues and related plans to the Chairman.
- Organize at least two information security education and training sessions annually to enhance the overall staff's awareness of information security.
- Regularly conduct red team exercises, vulnerability scanning, penetration testing, and email social engineering drills to continually strengthen the strength of information security defense capabilities.
- The company has implemented international information security standards, such as ISO 27001, and has gradually obtained certification. It successfully passed the ISO 27001 certification on August 16, 2022, and the certificate is valid from October 24, 2022, to October 24, 2025.
ISO 27001 Certificate (2022/10/14-2025/10/24) - The company has implemented information security solutions to enhance and monitor system and network security.
V. Emergency Notification Procedures
When a cybersecurity incident occurs, the responsible unit must assess the severity of the incident and report it to the Information Security Department and relevant units according to the incident level. The incident should be resolved within a specified timeframe.